April 09, 2024
Increase Database Security With Static IP Support in Prisma Accelerate
Prisma Accelerate introduces Static IP support, enabling secure connections to your database with predictable IPs for controlled access and minimized exposure. This allows connections from Accelerate to databases requiring trusted IP access.

Limit database access with IP allowlisting
When building data-driven apps, it's important to prioritize database security. This is because the database holds the application data, often containing sensitive user information, which needs to be protected. It’s standard practice to adopt a layered approach to improve database security, whereby you layer protection mechanisms on top of each other to protect your database.
Some of the security measures that can be considered include:
- Password or mutual TLS authentication.
- Firewall and IP allowlists to only allow database access from known hosts.
- Using private networking and VPCs to isolate database access from public internet.
- Using TLS (Transport Layer Security) to ensure that all traffic is encrypted.
- Principle of least privilege whereby each entity/component (person, service account) has the minimum necessary access rights to perform its purpose.
By layering these defenses, you can better protect your database from various types of attacks and reduce the chances of a security breach.
To add one layer of these security measures, you can restrict database access from the public internet by configuring firewalls and IP allowlists to limit access to trusted IP addresses. It becomes possible if the IP addresses that require access to your database are static IP addresses.
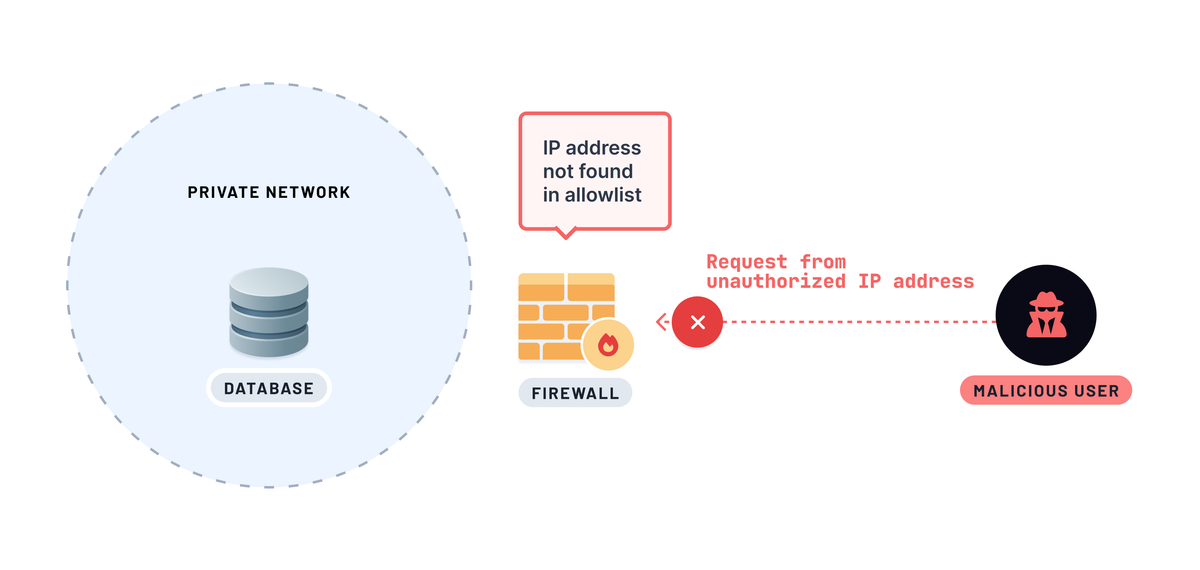
A static IP address is an IPv4 or an IPv6 address that doesn’t change. Unlike dynamic IP addresses, which can change unpredictably, traffic from static IP addresses are easier to identify.
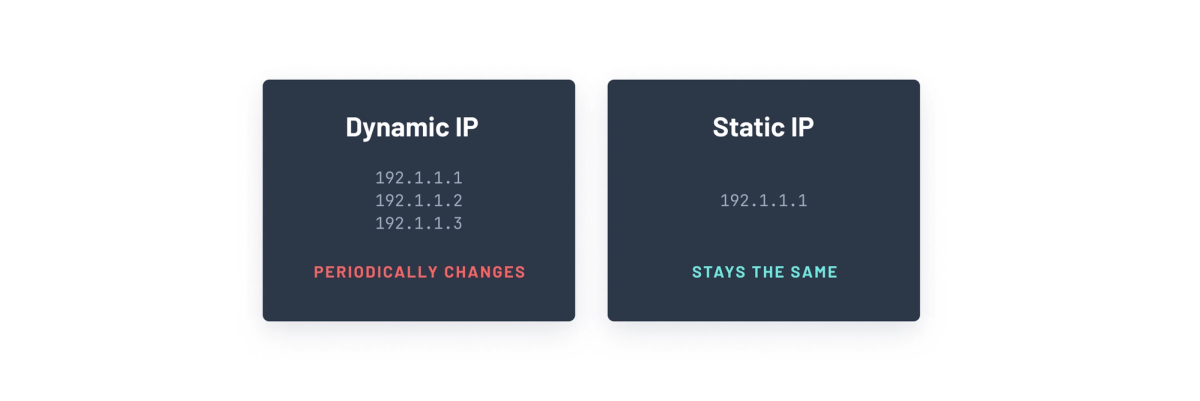
Using static IP addresses benefits managing and securing traffic by allowing you to configure your network firewalls or set up IP allowlisting to restrict access to your resources from specific IP addresses that don’t change.
Enabling static IP within your Prisma Accelerate configuration in a project environment allows using Accelerate with databases that have IP allowlisting enabled.
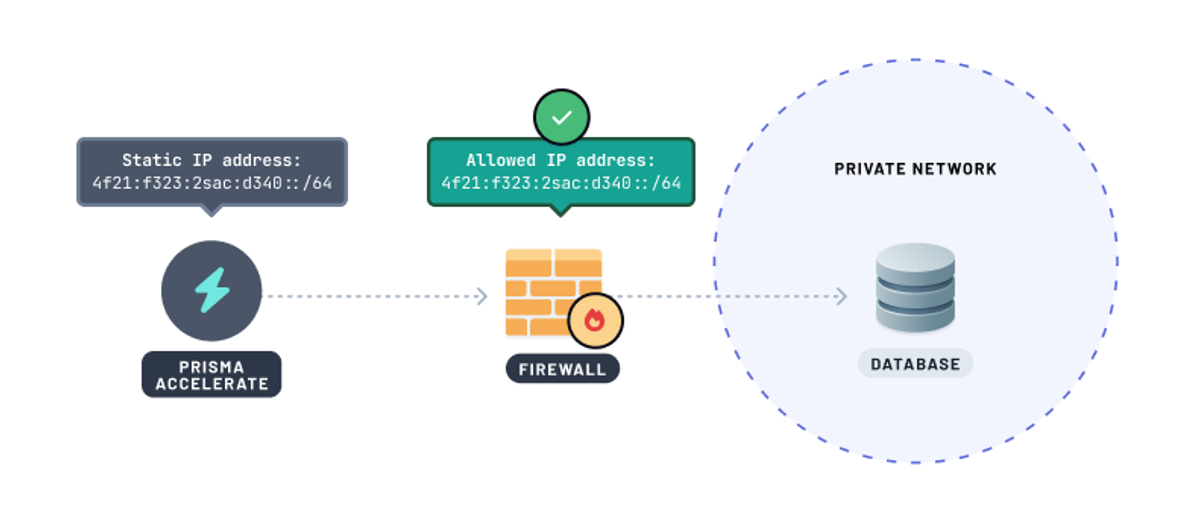
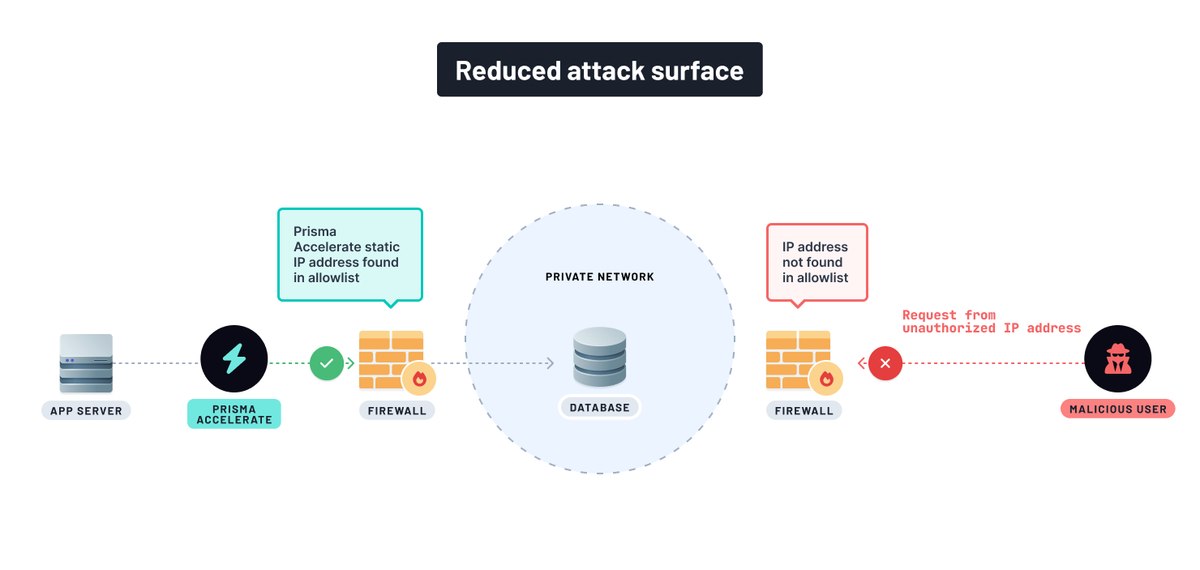
You can add the Accelerate static IP address in the database firewall IP allowlist or permit access to the IP address within your private network. This ensures that Accelerate can securely access your database while other unauthorized requests to your database are denied.
Enable static IP in Prisma Accelerate
To enable static IP support for Accelerate within your existing or new project environment, ensure you’re on our Pro or Business plan. Refer to our pricing page for more information.
📒 Enabling static IP in your Accelerate setup won't interrupt active connections.
Users can opt-in to using static IP in the Platform Console in two ways:
-
When enabling Accelerate for your project environment, opt-in to static IP after specifying your database connection string and connection pool region.
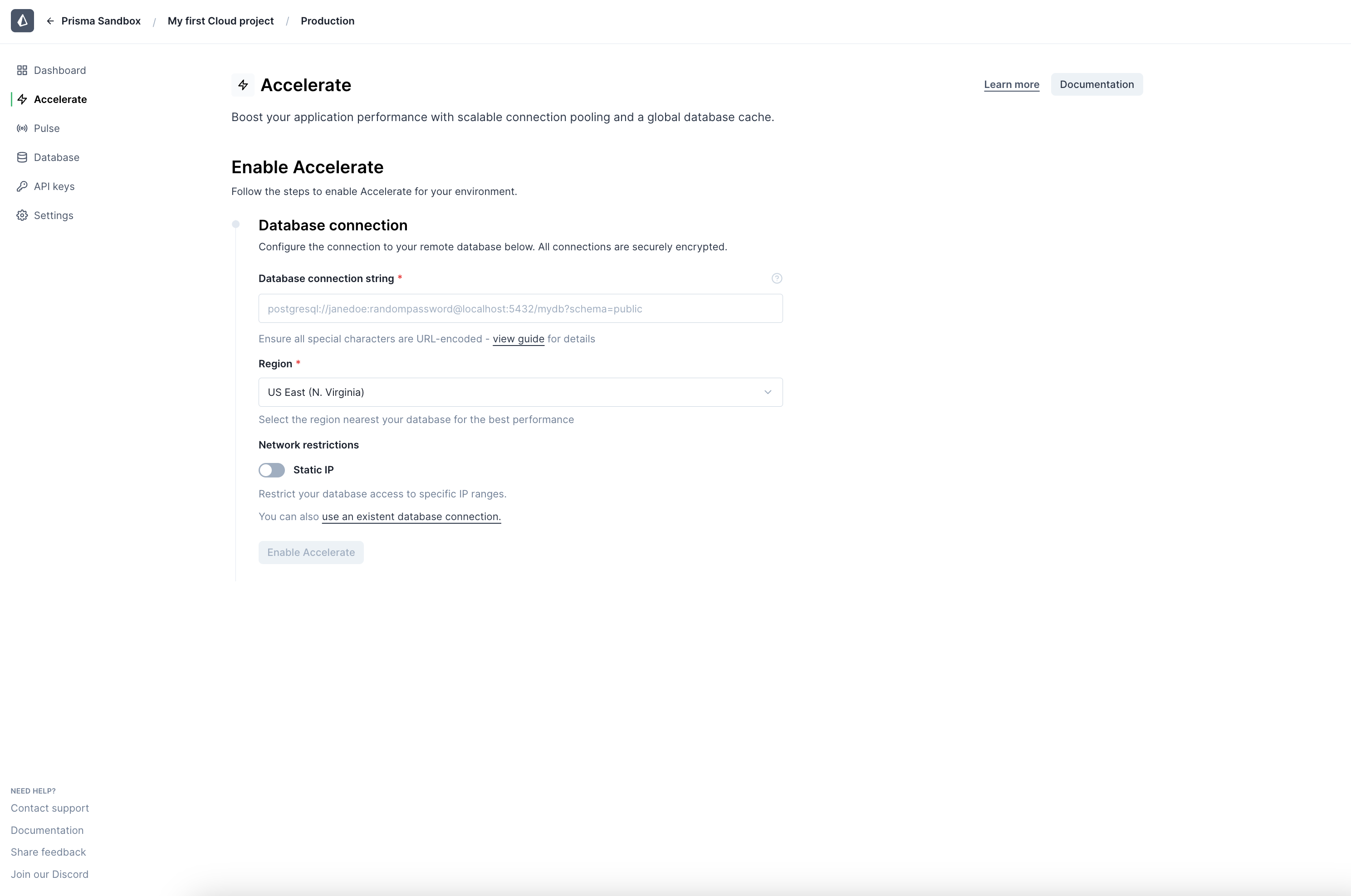
-
For projects already using Accelerate, enable static IP by navigating to Accelerate settings in your project environment.
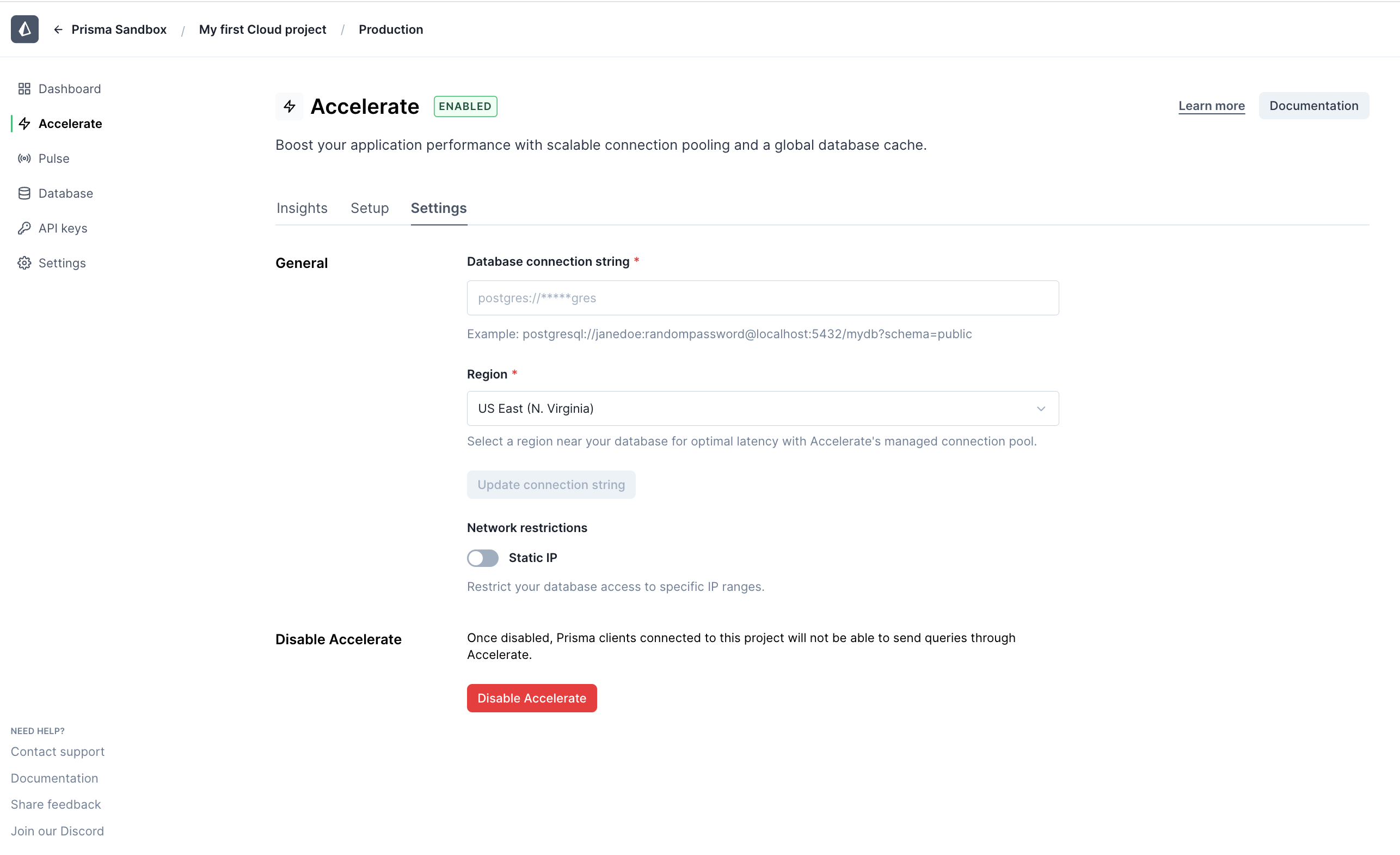
After you enable static IP within your Prisma Accelerate configuration, you’ll see a list of IPv4 and IPv6 addresses , which you will use to allow Accelerate traffic to your database.
Setup your database with Accelerate’s static IP
Configure your database firewall to limit incoming connections to trusted IP addresses. Once static IP is enabled within your Prisma Accelerate configuration in a project environment, adding them to your database provider varies depending on the provider. We’ll look at one example to understand how to configure IP allowlists for a database hosted on MongoDB Atlas.
Configure IP access list entries in MongoDB Atlas
Here's how to restrict incoming connections to your MongoDB Atlas-hosted database to originate only from Prisma Accelerate:
- Enable static IP for Prisma Accelerate in your project environment.
- Copy the IPv4 addresses.
ℹ️ MongoDB Atlas currently only allows you to add IPv4 addresses in the IP allow list.
- Add the IPv4 addresses to your MongoDB Atlas network allow list:
📒 Visit the MongoDB docs for more info on managing IP access to your database.
- Go to your MongoDB Atlas project dashboard.
- In the Security section of the left navigation, click Network Access. The IP Access List tab displays.
- Click ➕ Add IP Address.
- Then in the popup titled Add IP Access List Entry, keep adding the IPv4 static IP addresses you copied earlier in the Access List Entry field. Optionally, you can name the entry by adding a comment in the Comment field, for example, "Accelerate IP", to identify the static IP address later.
- Click Confirm to complete the step.
- Delete other IP addresses, such as an IP address entry
0.0.0.0/0, which allows public access to your database by clicking on the Delete button in the Actions column.
And you’re done! In a few steps, you’ve added a layer of security to your MongoDB database, ensuring Prisma Accelerate can access your database while unauthorized access requests are denied.
Make your database more secure
Database security is increasingly important for data-driven apps, and adding an extra layer of protection to your database can reduce the risk of exposing sensitive data.
In just a few steps, you can increase the security of your database and make sure Accelerate can still access your database while access requests from unauthorized IPs are denied.
If you need any help or have questions, reach out to us in our Discord community.
Go to Platform Console
Share with us your experience with Prisma Accelerate via a post in our X. And to stay updated on new exciting feature releases, keep an eye on our changelog.
Don’t miss the next post!
Sign up for the Prisma Newsletter
